Cayla, a computer driven talking doll, uses technology similar to that behind Amazon’s Alexa, Microsoft’s Cortana, Apple’s Siri, and Google Home to construct a toy that simulates a living friend for a child. Unfortunately, some believe that Cayla may be the embodiment of the murderous Talky Tina of the fifty-year-old episode of The Twilight Zone, The Living Doll.
In Germany, Cayla has been declared a banned surveillance device. Selling and even possessing a Cayla in Germany is illegal. The doll’s communication capability must be permanently disabled to make it legal in Germany. Also, several groups in the US have launched an action to have Cayla sanctioned under the Children’s Online Privacy Protection Act (COPPA).
I’m not here to advocate that these government and legal actions are justified or not justified, that’s for individuals to decide for themselves, but I think anyone who is concerned about cybersecurity should understand some of the issues involved. We are likely to see many more products like Cayla appearing on the market. Some will be for children, others for teens, and many aimed at adults. Some will be great, some exploitative, and some will, no doubt, be just plain shoddy.
So let’s take an engineer’s look at Cayla. The complaint document sent to the Federal Trade Commission is against Genesis Toys and Nuance Communications and was lodged by the Electronic Privacy Information Center and Consumers Union, among others. Genesis Toys is a Hong Kong corporation that developed the doll. Nuance Communications is a US corporation that retains and processes data collected by the Cayla doll. The exact relationship between Genesis and Nuance is not clear to me, but they are two separate corporations.
Cayla’s architecture is fairly simple. The doll itself is the equivalent of a Bluetooth headset that acts as a microphone and speaker for an app that runs on a smartphone, like an iPhone or an Android. The app communicates with a cloud service that supplies computing and storage resources that power Cayla.
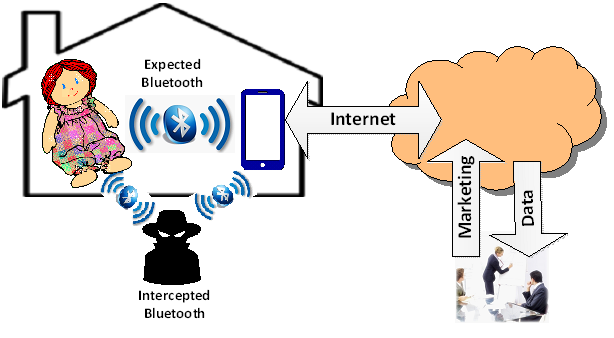
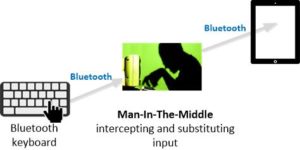
This architecture has issues. Bluetooth headsets are insecure. I mentioned in a blog a few months ago that the NSA has banned commercial Bluetooth headsets for classified or confidential information. Here. A criminal hacker would not have much trouble listening in on a child’s conversations with Cayla and interjecting their own questions and suggestions. Imagine a pedophile speaking through Cayla suggesting to a three-year-old that they meet out in the street. The Bluetooth standard says the protocol is good to ten meters (30 feet) but special equipment can extend the range substantially. Also, Bluetooth signals, essentially the same as Wi-Fi, penetrate walls.
Even in isolated spots where Bluetooth intrusion may not be a consideration, Cayla has vulnerabilities. The FTC complaint points out that Cayla is programmed to promote certain commercial products, such as movies. In addition, the information that Cayla collects, like names, locations, favorite foods and toys, etc., is stored in the cloud. The Genesis Toys privacy policy states that this information is kept and analyzed by Nuance Communications and may be shared. I should note that while I was writing this blog, the posted Genesis privacy statement was changed. You may want to check it for yourself.
Cayla simulates conversation, answers and asks questions, and can, or potentially can, do all of the things Alexa, Cortana, Siri, and Google Home can do: order pizza, open the front door, adjust the thermostat, call for an Uber. The list gets longer every day. Cayla can’t do all these things now, but the technology she is built upon can. Cayla’s limits are set by the discretion of Genesis Toys and Nuance Communications. Parents may want to be certain that controls are in place that will prevent their three-year-old from ordering a dozen pizzas or their ten-year-old embarking on a trip to Aruba. I don’t suggest that Cayla is likely today to cause these things to happen. Rather, parents should be aware that these new products make such mishaps possible.
Like the living doll on Twilight Zone, Cayla is a new technology with unexpected powers and these powers can harm us if they are not used properly.
In another blog, I plan to discuss the steps I would take when deciding whether I want a product like Cayla in my home. These products have amazing potential for improving our lives and could be more fun than a barrel of monkeys for our children. But they can also be dangerous. You should choose with knowledge and good judgement.