In a comment on a previous post, Steve Stroh suggested explaining the nuances of routable and non-routable addresses. This distinction is important for home network security, but without a little background in computer networking, the concept doesn’t mean much. This post explains a little about how the global computer network operates.
Traditional telephone service
I’ll begin with traditional telephone service works because, without realizing it, most people have it tucked away somewhere in their brain that computer networks work like an old telephone system.
Circuits
Traditional telephones are based on circuits. Imagine an old-fashioned switch board with a bunch of incoming wires and outgoing sockets. When an incoming wire from your phone is plugged into an outgoing socket a circuit is completed and you can speak to and hear a person on a telephone at the other end of the circuit.
In a simple time, when Fred and Ethel were struggling performers, they both roomed at The Algonquin. Its switch board could manage the handful of telephones in the hotel. Fred could pick up his phone, tell the switch board operator to connect him to Ethel, a circuit between Fred’s phone and Ethel’s phone was made and Fred and Ethel could plan, dream, and toss whoopie.
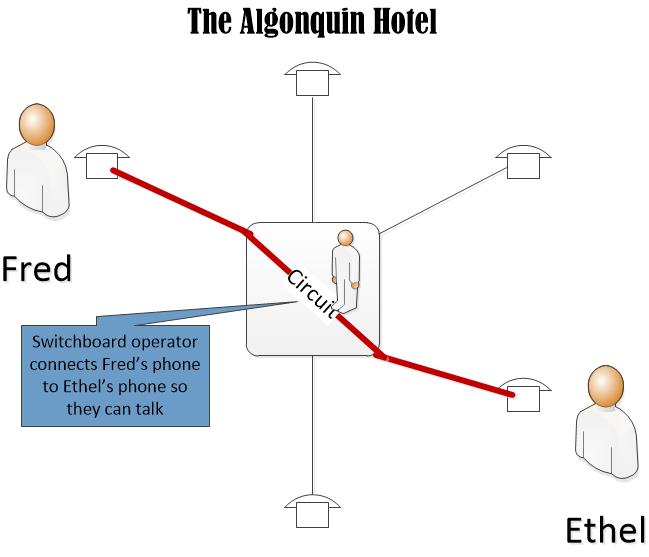
When Ethel’s fan dance made headlines, she moved to The Ritz. Fred, who was a baggy pants comic with a fake Yiddish accent, was stuck at the Algonquin. For Fred to call Ethel, the Algonquin operator had to connect to the Ritz operator, who then connected Fred’s line into Ethel’s phone. Unfortunately, Ethel no longer talked to lowlifes like Fred and she immediately hung up. The operators unplugged the lines, and the circuit was gone.
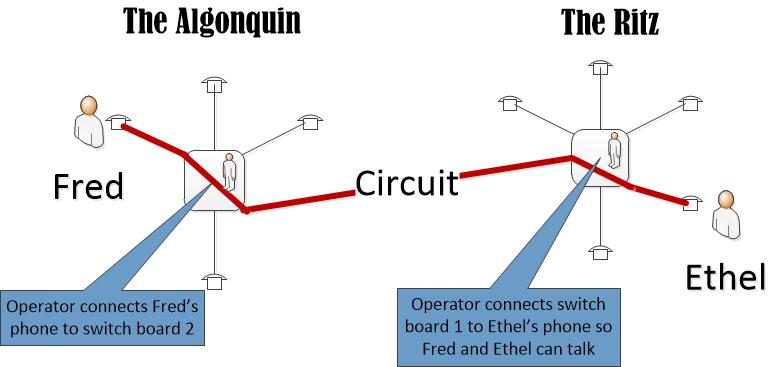
The pattern of connecting switch board to switch board was repeated until the phone network covered the entire U.S. and transoceanic cables extended the network to Europe. Getting a connection could take hours, but the system worked. Over time it was automated, first by mechanical relays, later by transistors and computer chips. Connections became faster. Nonetheless, for most purposes, the circuit system was eventually abandoned in all but metaphor.
Packet switching
Computer networks replaced circuits with an older approach: mail packets.
Mail works differently than the telephone. Writing an address on an envelope is only superficially similar to dialing or asking an operator for a phone number. When you drop an envelope in the mail, you have a promise that the post office will try to deliver it, but that promise is no guarantee and the office that first receives the letter is likely not to have any knowledge of the letter’s destination.
A mailbox will accept a letter addressed to T. H. E. Wiz, 1 Emerald Way, Oz, Kansas without a murmur, although neither T.H.E Wiz, Emerald Way, nor Oz exists in Kansas. You may or may not find out later your letter was undeliverable. It will rattle around the postal system until it is eventually returned or falls into a dead letter bin.
On the other hand, try dialing a stage number, like The Bionic Woman’s number, 311-555-2368. You are told that a connection is impossible as soon as you finish dialing.
The crucial difference is that before your message is transmitted by phone, i.e. you begin to speak, the path you will use to communicate is either is made or fails. The postal system, on the other hand, accepts your message, then passes it on until it lands in an office that recognizes the address and the intended recipient.
Circuits v. packets
Off-hand, the telephone seems like the smarter way. Why go to all the trouble of shipping an envelope around the country when you can decide before sending the message if delivery is possible? Isn’t the post office method a step backward?
Well, no. Circuits may seem more efficient, but they don’t fit well into the reality of the global internet, which is huge, ever changing, and implemented in a patchwork of wildly varying speed and reliability; a salmagundi of large and small, public and private entities that is closer to a frontier pony express than an orderly telephone system.
No single entity understands the complexity of the global network. However, piecing together a workable, let alone optimal, circuit requires just that.
A typical computer message is broken up into a series of independent small packets, each with its own address. These are dumped willy-nilly into the network and each is passed from router (the computer equivalent of a switchboard or a post office) to router until they arrive at their destination and are reassembled. Some will be duplicated to be sent on alternate routes or further broken down into smaller packets to optimize transmission on equipment that can’t handle large packets. The process is messy, but resilient and makes good use of available resources.
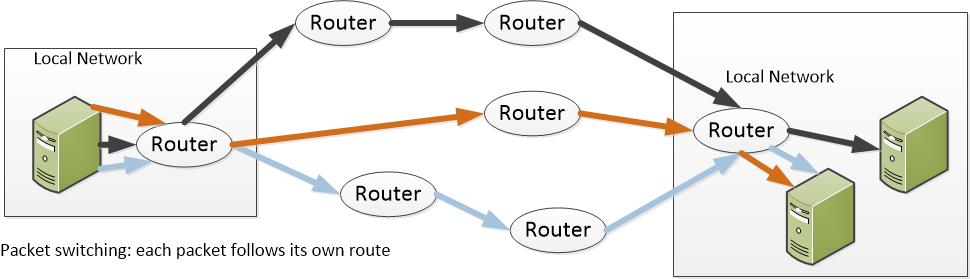
Packets in the network hop from router to router approaching light speeds, i.e. almost instantaneously, but then they sit in a buffer while the router decides what to do with it. A packet can hop to another router faster than a router can respond to a query on traffic conditions, so why bother asking? Sending packets to find their own way only requires local knowledge of the condition of the communications infrastructure. With a network as extensive and varied as the global computer network, this is a critical advantage.
Today, most telephone service, including cellphones, travels in switched packets that simulate circuits. We still tend to think of a single wire connection that runs from one phone to the next through a myriad of automated switch boards, but in fact most of the time, our voice is carried in packets drifting through a global network.
Permanent (static) addresses
In the old days, computer addresses, IP addresses, were more or less permanent. Businesses requested and were assigned blocks of addresses. A system administrator had to keep track of those addresses and dole out new addresses from the list as computers were added to the network and return old addresses to the available list as computers were decommissioned.
It was an exacting job. If the list got scrambled and two devices used the same address, the network would behave erratically. Small businesses typically had only a few addresses, which limited the number of computers they could use.
Private non-routable addresses
Giving every computer a public IP address was also a security problem. Each of those publicly addressed computers were vulnerable to direct outside attacks. They had to be managed carefully to prevent intrusion. Individual users seldom had the training and temperament to do that job well.
A solution from the mid-1990s was to declare blocks of addresses private or non-routable. The largest private block (10.0.0.0 – 10.255.255.255) has over 17 million individual addresses. The second block (172.16.0.0 – 172.31.255.255) over a million addresses. The smallest block (192.168.0.0 – 192.168.255.255) has over 65 thousand addresses.
This had lots of advantages. System administrators could devise address assignment schemes for the private address blocks that were relatively easy to manage with subsets for buildings, floors, departments, etc. and not worry about clashing with other businesses. Since the addresses were non-routable, computers with private addresses were easier to isolate from intruders.
Dynamic Host Control Protocol (DHCP)
The process of assigning and re-assigning IP addresses was automated with Dynamic Host Control Protocol (DHCP). When a computer connects to a home network, the home router, following DHCP rules, assigns the computer an IP address from one of the private blocks. Which block depends on how DHCP is implemented on the router.
When an Internet service provider connects a home router to the global network, the service provider uses DHCP rules to assign a unique public and global IP address to the home router.
Network Address Translation (NAT)
From the outside, each home network looks like a single computer with one IP address. This presents a problem: how to connect those internal private addresses with the single outward-facing address. Non-routable private IP addresses combine with DHCP and Network Address Translation (NAT) to solve this problem. Network Address Translation (NAT) is a protocol implemented on routers that handles coordinating internal non-routable IP addresses with the single external public IP address that the router presents to the global network.
Without private addresses, DHCP, and NAT, connecting a new computer to a home network would be a tricky and exacting job. I won’t say that connecting a new device is easy today, but I assure you, when I think about managing networks thirty years ago, I am amazed. Our grandsons have our wireless network id and password stored on their phones and laptops. When they walk into our house, their laptop or phone connects with our wireless network, an IP address is assigned, and they connect with the global network without me doing anything. Astounding!